trs96
Moderator
- Joined
- Jul 30, 2012
- Messages
- 25,535
- Motherboard
- Gigabyte B460M Aorus Pro
- CPU
- i5-10500
- Graphics
- RX 570
- Mac
- Mobile Phone
This is pretty serious for Mac and CustoMac users. If you see this OS X Updates pop up, just shut down your Mac by pressing and holding the power button, don’t enter your password. Turn off your internet. When you sign back in you can remove that malware from startup. Use something like CCleaner for Mac to do this easily. Apple has already revoked the certificate so you should be ok. Note: It's easy to tell this is not from Apple. They don't call Sierra OS X anymore it's macOS now.
Article is by Killian Bell from Cult of Mac
OSX/Dok, a new strain of “major scale” malware targeting macOS users, can bypass the Gatekeeper feature that’s designed to block malicious software.
The newly identified trojan, which prevents you from doing anything on your Mac until you install a bogus software update, also goes undetected by many antivirus programs.
As the macOS user base grows, so does the malware that targets it. According to McAfee Labs, malware attacks designed for Mac computers rose 744 percent in 2016, with almost 460,000 samples discovered. The latest is particularly worrisome.
Uncovered by security researches at Check Point, OSX/Dok can hit all versions of macOS and OS X. It wasn’t recognized by antivirus databases when it was first discovered, and it is considered by be the first “major scale malware” to target Mac users.
OSX/Dok malware targets all Macs
The most troublesome aspect of this malware? It is signed with a valid developer certificate that’s been authenticated by Apple, which means macOS doesn’t see it as a threat and it isn’t blocked by Gatekeeper. The certificate is dated April 21, 2017.
“Once OSX/Dok infection is complete, the attackers gain complete access to all victim communication, including communication encrypted by SSL,” explains Check Point. “This is done by redirecting victim traffic through a malicious proxy server.”
The malware is being distributed primarily in Europe via phishing emails that encourage users to download a file that details supposed inconsistencies in their tax returns. That file is named “Dokument.zip” when distributed among users in Germany.
How OSX/Dok Mac malware works
When you open it, the malware copies itself to the /Users/Shared folder, then proceeds to execute itself automatically. It also removes any trace of the original download from the Downloads folder, and presents an error message that hopes to convince users the file “could not be opened.”
Little do they know that the malware has added itself as a Login Item with the name “AppStore,” which runs automatically when they first start up their Macs. It will continue to execute every time an infected Mac is started up until it has successfully installed its payload.
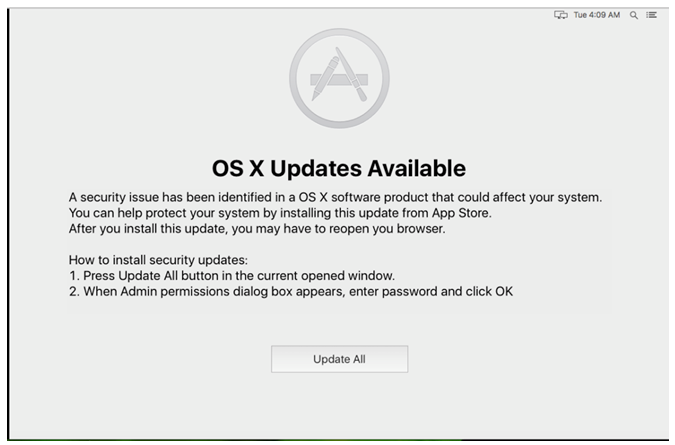
“The malicious application will then create a window on top of all other windows. This new window contains a message, claiming a security issue has been identified in the operating system that an update is available, and that to proceed with the update, the user has to enter a password.”
Once you have received this popup, you cannot do anything with your Mac until you agree to install the bogus update. And of course, entering your password provides the malware with administrator privileges and it can continue the next phase of its assault.
That includes installing a package manager that downloads and installs additional tools, and providing the existing user account with admin privileges immediately without the need to enter a password. It also alters network settings to ensure all outgoing connections pass through a proxy.
What OSX/Dok Mac trojan does
Of course, that proxy sits on a malicious server on the “dark web,” and every piece of data that passes through it gets collected.
“As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings,” Check Point says.
“The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim’s traffic and tamper with it in any way they please.”
Once the attacker has obtained the information they want, the malware will remove itself from the infected machine. The user has no idea what was going on in the background until it’s too late.
Article is by Killian Bell from Cult of Mac
OSX/Dok, a new strain of “major scale” malware targeting macOS users, can bypass the Gatekeeper feature that’s designed to block malicious software.
The newly identified trojan, which prevents you from doing anything on your Mac until you install a bogus software update, also goes undetected by many antivirus programs.
As the macOS user base grows, so does the malware that targets it. According to McAfee Labs, malware attacks designed for Mac computers rose 744 percent in 2016, with almost 460,000 samples discovered. The latest is particularly worrisome.
Uncovered by security researches at Check Point, OSX/Dok can hit all versions of macOS and OS X. It wasn’t recognized by antivirus databases when it was first discovered, and it is considered by be the first “major scale malware” to target Mac users.
OSX/Dok malware targets all Macs
The most troublesome aspect of this malware? It is signed with a valid developer certificate that’s been authenticated by Apple, which means macOS doesn’t see it as a threat and it isn’t blocked by Gatekeeper. The certificate is dated April 21, 2017.
“Once OSX/Dok infection is complete, the attackers gain complete access to all victim communication, including communication encrypted by SSL,” explains Check Point. “This is done by redirecting victim traffic through a malicious proxy server.”
The malware is being distributed primarily in Europe via phishing emails that encourage users to download a file that details supposed inconsistencies in their tax returns. That file is named “Dokument.zip” when distributed among users in Germany.
How OSX/Dok Mac malware works
When you open it, the malware copies itself to the /Users/Shared folder, then proceeds to execute itself automatically. It also removes any trace of the original download from the Downloads folder, and presents an error message that hopes to convince users the file “could not be opened.”
Little do they know that the malware has added itself as a Login Item with the name “AppStore,” which runs automatically when they first start up their Macs. It will continue to execute every time an infected Mac is started up until it has successfully installed its payload.
“The malicious application will then create a window on top of all other windows. This new window contains a message, claiming a security issue has been identified in the operating system that an update is available, and that to proceed with the update, the user has to enter a password.”
Once you have received this popup, you cannot do anything with your Mac until you agree to install the bogus update. And of course, entering your password provides the malware with administrator privileges and it can continue the next phase of its assault.
That includes installing a package manager that downloads and installs additional tools, and providing the existing user account with admin privileges immediately without the need to enter a password. It also alters network settings to ensure all outgoing connections pass through a proxy.
What OSX/Dok Mac trojan does
Of course, that proxy sits on a malicious server on the “dark web,” and every piece of data that passes through it gets collected.
“As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings,” Check Point says.
“The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim’s traffic and tamper with it in any way they please.”
Once the attacker has obtained the information they want, the malware will remove itself from the infected machine. The user has no idea what was going on in the background until it’s too late.
Last edited:
